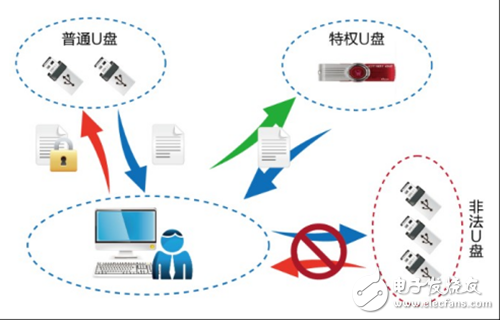
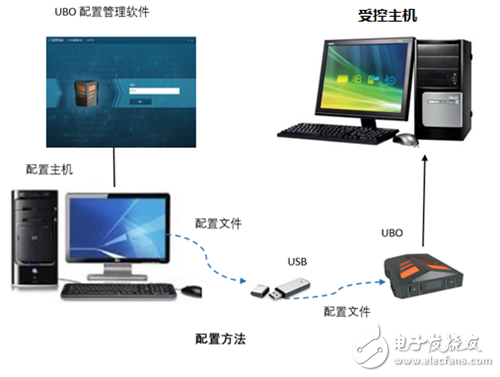
USB attacks are common and security protection needs to be strengthened. A former National Security Agency officer told the Los Angeles Times that "normally, employees are forbidden to use U disk in the office, but there are exceptions, especially for network managers like Snowden, who can carry U disk." . It can be seen that in the management of USB operation behavior, artificially established constraints do not completely guarantee information security. And with the development of USB attack technology, there are even new USB attack methods such as "USB bomb". A USB bomb experiment video was broadcast on the Internet. In the video, the Russian security researcher inserted the USB flash drive into a brand new laptop. After a few seconds, the notebook was completely destroyed, and the entire USB attack process was automated. It is understood that the USB bomb looks the same as other USB flash drives. When plugged into the device, it is equipped with a small capacitor that can draw power from the device, quickly charge itself, and discharge more than 200 VDC power to the host within one second. The host burns, the data is eliminated, and the whole process is in a matter of seconds. As a standard interface for computer data transmission, USB has been widely used. However, in the investigation of the enterprise's information security protection system, it is learned that enterprises pay more attention to the security of networks, systems, and Web applications, and often ignore the USB security protection, which leaves the hacker with an opportunity. In the past USB attack incidents, the company's core data leakage, research results were stolen, equipment was damaged, and so on, enterprises must strengthen USB security protection. UOB, a professional USB protection device Based on in-depth research on various attacks and virus samples implemented in recent years for USB, the company has independently developed a highly technical forward-looking hardware-wide USB protection product, UBO, based on intelligent learning. The engine protects against new advanced USB attacks. And through the three methods of vulnerability monitoring and defense, authority management, and operation behavior record, the USB device is fully and effectively protected. UBO has filled the gap in the security protection technology of domestic products in the field of USB attacks. It is the most comprehensive and reliable product for USB protection in China, and can meet government, finance, confidential units, military, military, energy, manufacturing. The need for computer security and document leakage prevention in different industry systems such as transportation, enterprises, petroleum and petrochemicals. (Youbao UBO-USB Security System) Vulnerability monitoring and defense, huge vulnerability library to support According to statistics, billions of USB devices worldwide are threatened by BadUSB, and other new advanced USB attacks such as USB bombs, LNK attacks, and death blue screens threaten users' information security. In order to solve the threat posed by USB attacks to enterprises, 匡en Network organizes a professional research team to explore and research the latest USB attack methods and apply the defense technology to UOB products. UBO UBO has a comprehensive library of USB attack vulnerabilities, including open vulnerabilities and undisclosed vulnerabilities discovered independently by Jen. Advanced USB attack U disk classification management, intelligent authority allocation According to the 2017 Global Information Security Survey, 44% of information leaks because the management of internal personnel is not in place, but the constraints imposed by humans cannot guarantee information security. How to restrict the management of personnel rights is the key factor to ensure enterprise information security. one. Youbao UBO-USB security protection system uses the permission control mechanism to register and authenticate the USB device and control the scope of use. It restricts the USB device from randomly transmitting the intranet data to prevent the leak caused by the lack of permission management. In the authentication process, UBO UBO is mainly divided into privileged U disk, ordinary U disk, and illegal U disk. The privileged U disk can read and write data in the USB bidirectionally; the ordinary U disk can only transmit to the PC data in one direction; the illegal U disk can not obtain any permission after accessing the UBO. UBO UBO replaces the previously established binding regulations, so that users can be deviceized, intelligent and efficient in the behavior management of U disk. (USB rights management) USB operation behavior record, traceability of security events When an enterprise has an information security incident, it is very important to trace the entire incident process. UBO UBO performs detailed logging on all operating actions of the USB port, including mouse and keyboard access, U disk access and read and write operation records, alarms and USB attack behavior, protection operations, etc., so that users can Trace important events, retain evidence and records. Configuration method "soft" and "hard" combination, safe and simple deployment In order to facilitate user product deployment, UOB UBO adopts independent hardware + heterogeneous software system design. Independent hardware structure, so that the user protected computer does not need to install software to avoid the impact of the protection product on the original working system; the heterogeneous software architecture makes the physical separation zone between the U disk and the computer, and the data file is pre-read. Handling, blocking the copy of malicious files and filtering files through the proprietary killing virus software of the company, thus ensuring the safe and reliable reading and writing of USB data.
Because the shape of this vape pen is similar to that of regular cigarettes, it produces a more familiar smoking experience, and as a result, this sort of e-cigarette gadget is highly popular. This Disposable Vape Pen is more smaller, lighter, and easy to travel and carry, in addition to being cost-effective and similar to smoking.
Features:
1. Strong throat hit, all characteristic flavors satisfy your taste buds.
2. No button at all, inhale and enjoy it immediately.
3. Streamline pocketable design, lightweight and portable.
4. Rubber painted surface, skin touch feeling, soft but non-slip.
3000 Puffs Disposable Vape, 3000 Puffs Vape Bar, 3000 Puffs Vape Pen, vape pen starting kits,vaping juice Mainstay (Guangdong) biotechnology Co., Ltd. , https://www.heyleme.com

Recently, the "Prime Gate Incident" disclosed by Snowden on the social networking site on whether Russia and the United States will extradite him back to China as a "transaction" video conversation, once again caused concern in the network security industry. At the beginning, Snowden brought the secrets from the National Security Agency through a simple computer USB flash drive. This incident caused the whole industry to pay attention to information security, especially the management of internal personnel rights.