Asymmetric encryption algorithm is a secret method of key. An asymmetric encryption algorithm requires two keys: a public key (publickey) and a private key (privatekey). The public key and the private key are a pair. If the data is encrypted with the public key, only the corresponding private key can be used for decryption; if the data is encrypted with the private key, only the corresponding public key can be used. Decrypt. Because encryption and decryption use two different keys, this algorithm is called an asymmetric encryption algorithm. The basic process of asymmetric information exchange for asymmetric encryption is: Party A generates a pair of keys and exposes one of them as a public key to other parties; Party B, which obtains the public key, uses the key to perform confidential information. After encryption, it will be sent to Party A; Party A will decrypt the encrypted information with another private key saved by Party A. On the other hand, Party A can use Party B's public key to sign the confidential information and then send it to Party B; Party B then uses its own private key to check the data. Party A can only use its private key to decrypt any information encrypted by its public key. Asymmetric encryption algorithms have better confidentiality, which eliminates the need for end users to exchange keys. The characteristics of the asymmetric cryptosystem: the strength of the algorithm is complex, and the security depends on the algorithm and the key. However, due to the complexity of the algorithm, the encryption and decryption speed is not as fast as the symmetric encryption and decryption. There is only one type of key in a symmetric cryptosystem, and it is non-public. If you want to decrypt it, you have to let the other party know the key. Therefore, to ensure its security is to ensure the security of the key. The non-symmetric key system has two kinds of keys, one of which is public, so that it is not necessary to transmit the other party's key like a symmetric password. This security is much bigger. 1. A wants to send information to B, both A and B generate a pair of public and private keys for encryption and decryption. 2. A's private key is kept secret, A's public key tells B; B's private key is kept secret, and B's public key tells A. 3. When A wants to send information to B, A encrypts the information with B's public key because A knows B's public key. 4.A sends this message to B (the message has been encrypted with B's public key). 5.B After receiving this message, B decrypts the A message with its own private key. Anyone else who receives this message cannot decrypt it because only B has the private key of B.
Aluminum Cell Phone Stand, Durable Cellphone,Desk Cell Phone Stand Holder Aluminum Phone Dock Cradle,etc.
Shenzhen Chengrong Technology Co.ltd is a high-quality enterprise specializing in metal stamping and CNC production for 12 years. The company mainly aims at the R&D, production and sales of Notebook Laptop Stands and Mobile Phone Stands. From the mold design and processing to machining and product surface oxidation, spraying treatment etc ,integration can fully meet the various processing needs of customers. Have a complete and scientific quality management system, strength and product quality are recognized and trusted by the industry, to meet changing economic and social needs .
Aluminum Vell Phone Stand,Aluminum Cell Phone Desk Stand,Cell Phone Holder For Stand,Cell Phone Stands Shenzhen ChengRong Technology Co.,Ltd. , https://www.dglaptopstandsupplier.com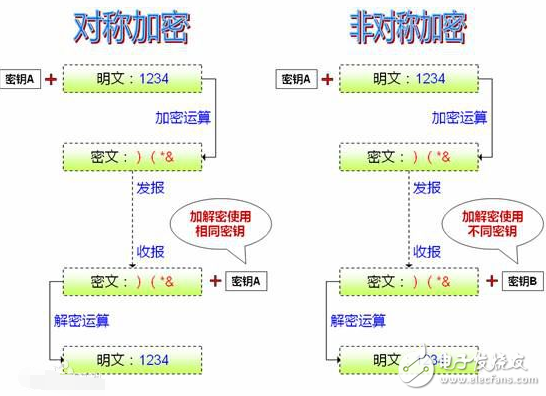
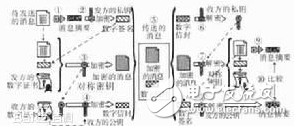

What asymmetric encryption algorithm